WHAT IS CTEM?
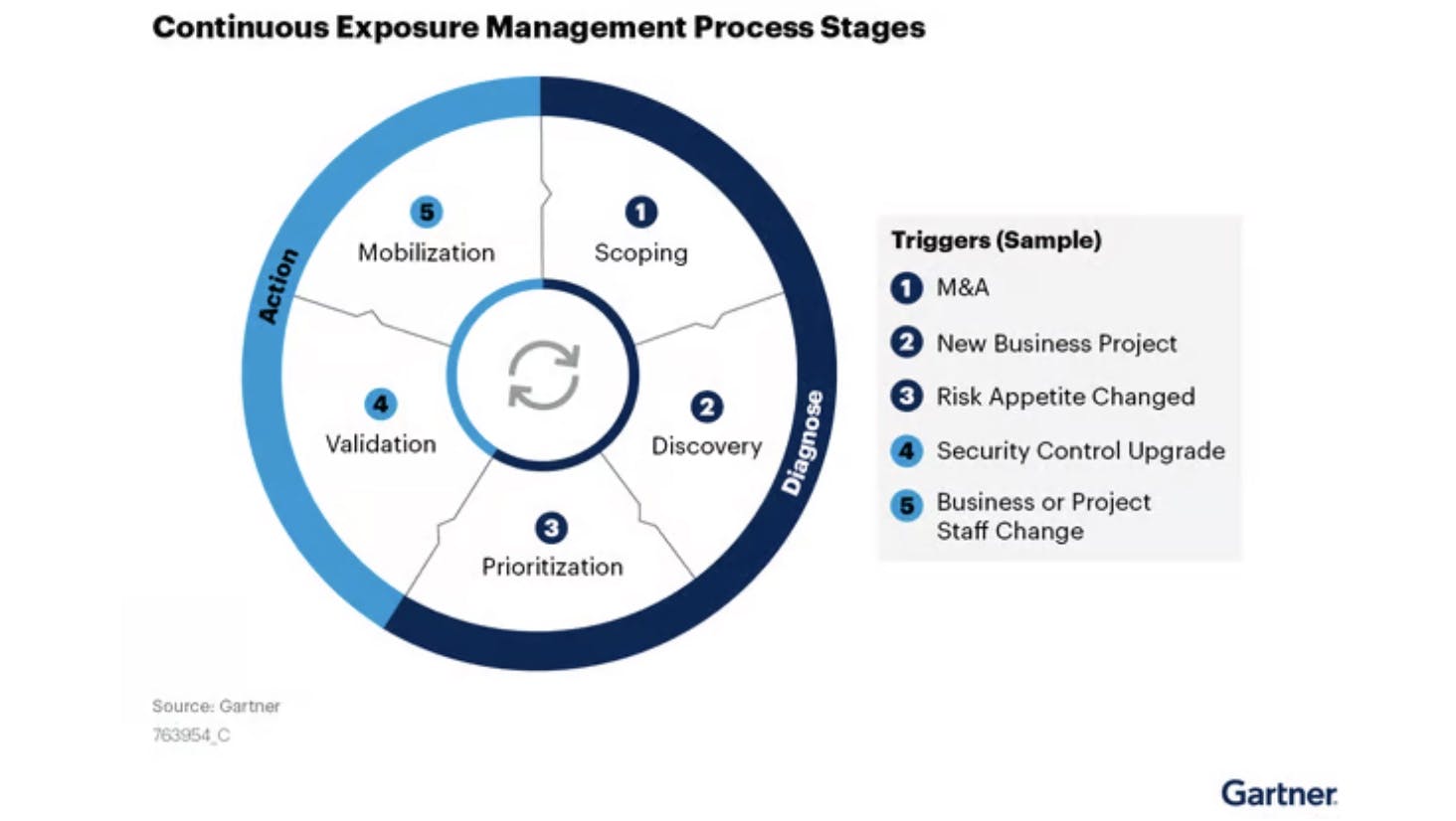
Continuous Threat Exposure Management (CTEM) curriculum and framework
The Limitations of Traditional Vulnerability Management
Traditional approaches to vulnerability management were often reactive and point-in-time:
Periodic Scans: Organizations would schedule infrequent scans, leaving them blind to new threats between scans.
Patch Overload: Remediation was overwhelming, with a massive volume of vulnerabilities to fix but limited resources to tackle them all.
Missing Context: Vulnerabilities were often viewed in isolation without understanding their overall business risk or the potential attack pathways.
The Rise of CTEM
Industry leaders, particularly Gartner, recognized that the threat landscape had changed significantly, necessitating a new, more dynamic approach. Here's why:
Expanding Attack Surfaces: With the cloud, IoT, and remote work, attack surfaces were growing exponentially, making point-in-time scans ineffective.
Increased Attacker Sophistication: Attackers were becoming more adept at chaining multiple lower-risk vulnerabilities together to create critical breaches.
The Need for Prioritization: Organizations needed to prioritize the vulnerabilities that posed the most immediate and significant business risk.

The CTEM Philosophy
CTEM shifts the focus from "finding everything" to "fixing what matters most." Key aspects include:
Continuous Assessment: Instead of occasional scans, CTEM leverages automated tools and techniques for near-real-time monitoring of the external and internal attack surface.
Attacker-Centric Thinking: CTEM simulates real-world attack techniques (like those used in breach and attack simulations), emphasizing how threats could actually be exploited.
Risk-Based Prioritization: Prioritization is based not just on vulnerability severity scores but on the likelihood of exploitation and impact on the business.
Focus on Remediation: CTEM emphasizes the importance of actually fixing critical vulnerabilities to improve organizational resilience.
Our Customers Speak
"I have gotten many infected emails this week. The Postini software has captured them and prevented a lot of problems. Thanks for all the great support I receive from NewPush."
Our Customers Speak
"We have experience with many hosts, normally it takes from hours to days to get things resolved. With NewPush I get responses fast, the last being in less than 5 minutes from the time I reported it. If your business depends on a company that is responsive and cares about your up time, then I would strongly suggest that you consider NewPush."
Our Customers Speak
"If you want a list of reasons I use NewPush, it would include great customer service, affordable fees, quick responses to my questions, and their proactive approach in assisting me to avoid common technology-related headaches. I refer my clients and my network of professionals to NewPush with complete confidence."
Our Customers Speak
"With the Connective Platform™ NewPush® deployed a vulnerability management solution that integrates our key security tools, and helps us enrich the data used by our SOC on a daily basis."
Our Customers Speak
"It was the ride of a lifetime to take my company from a startup featured at Interop to become a flagship product of a multi billion dollar company. NewPush was a key partner for over 15 years, they keep securing our SaaS solution delivered to household name clients on three continents."
Our Customers Speak
"Working with NewPush® for over 10 years, we have never missed compliance targets. Using the Connective Platform™ we are able to use best of breed security technologies and automate processes."